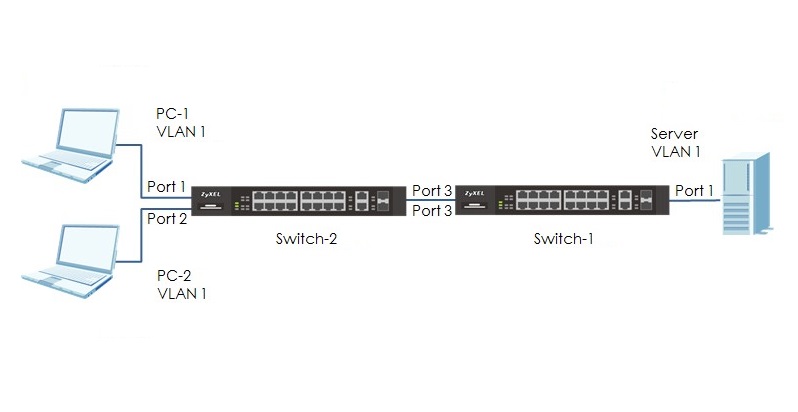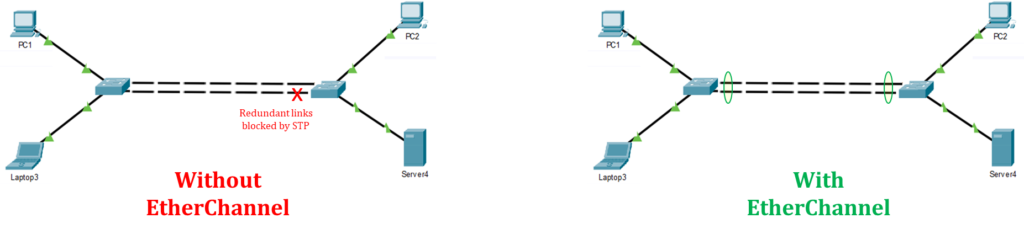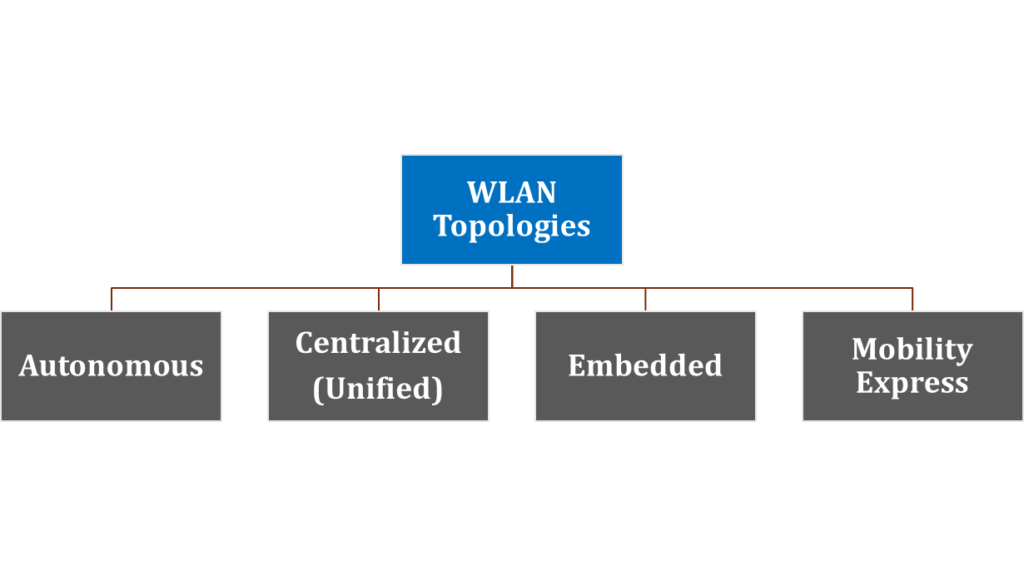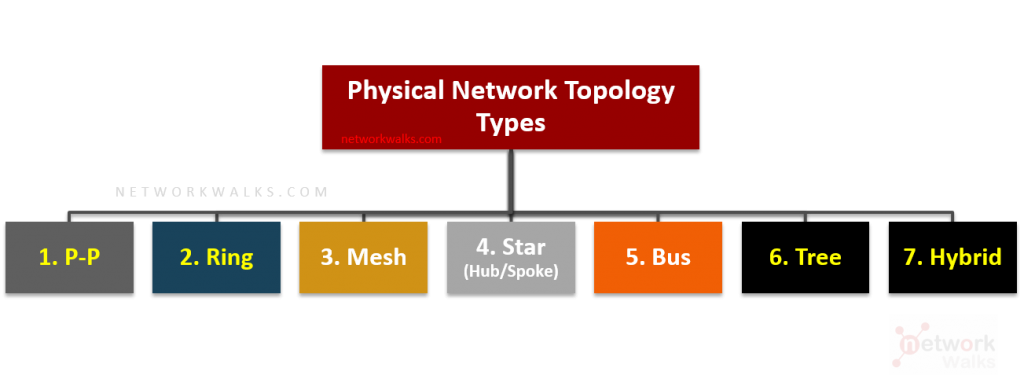
Network topology can be defined as the layout pattern and connectivity scheme between the devices in a network. It is simply the layout of network communication. There are two main types of Network topology, and they are Physical and Logical Network topology. Physical Network Topology: Physical topology is the actual connectivity or layout according to real cabling & connections Logical Network Topology: Logical topology is the virtual view of the network devices see Physical Topology Under the physical topology, there are about seven topologies: Point-to-Point Network Topology Star Network Topology Ring Network Topology Mesh Network Topology Tree Network Topology Bus Network Read More …