Understanding wireless & WiFi Roaming is very important in WLAN and WiFi computer networking. It occurs when a wireless client moves around in a region with many access points (APs). It may switch automatically to another access point (AP) with more preferred signal strength.
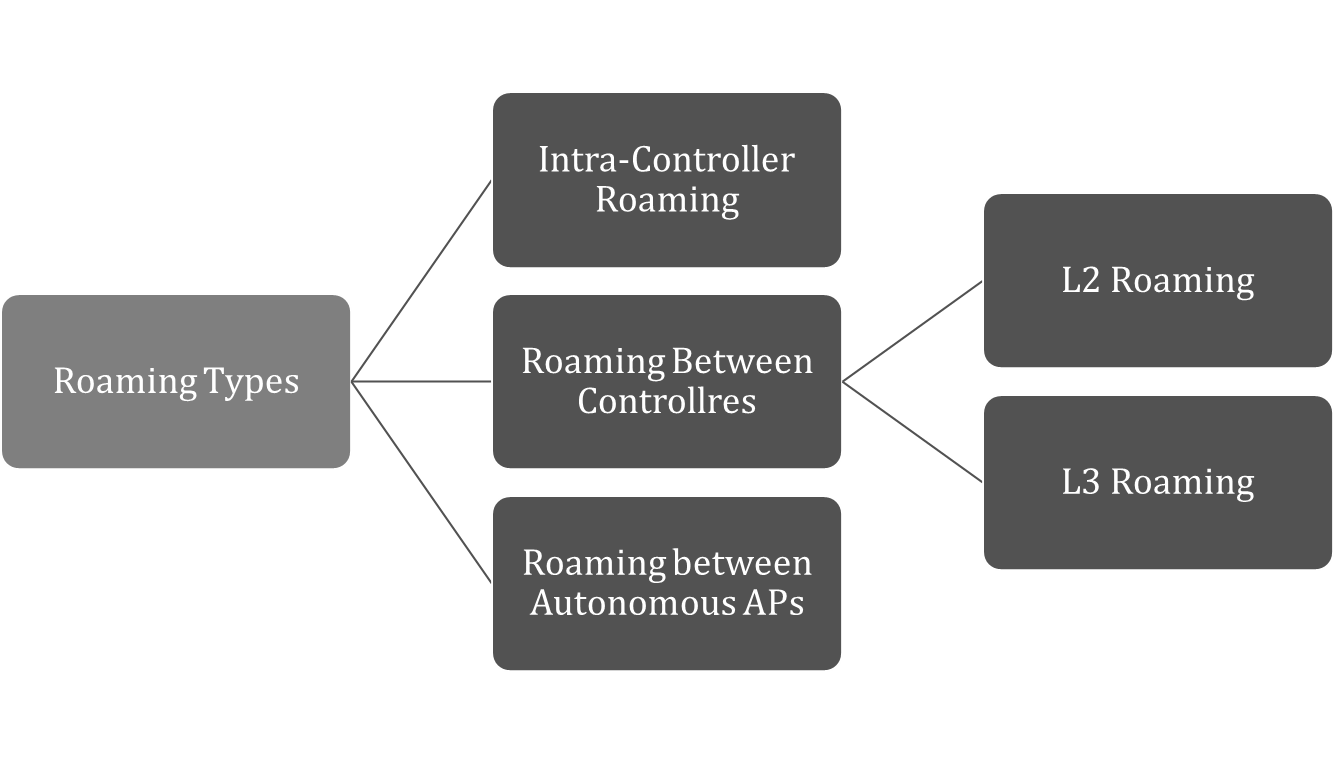
Understanding Wireless Roaming Types
The wireless roaming types are: Intra-Controller roaming, Roaming between controllers (L2 Roaming and L3 Roaming), and Roaming between Autonomous APs
Understanding Wireless & WiFi Roaming between Centralized Controllers
Also referred to as Inter-controller roaming. In this case, as the wireless network expands there are chances that the client needs to roam from one controller access point (AP) to another. Roaming between centralized controllers or inter-controller roaming are of two types: Layer 2 roaming and Layer 3 roaming
Understanding Wireless & WiFi Roaming between Autonomous APs
A client monitors the quality of the network continuously while moving, if the signal declines, the client looks for a different access point (AP) with a better signal. The process is quick and the client sends a probe request to locate a candidate access point (AP) and selects one
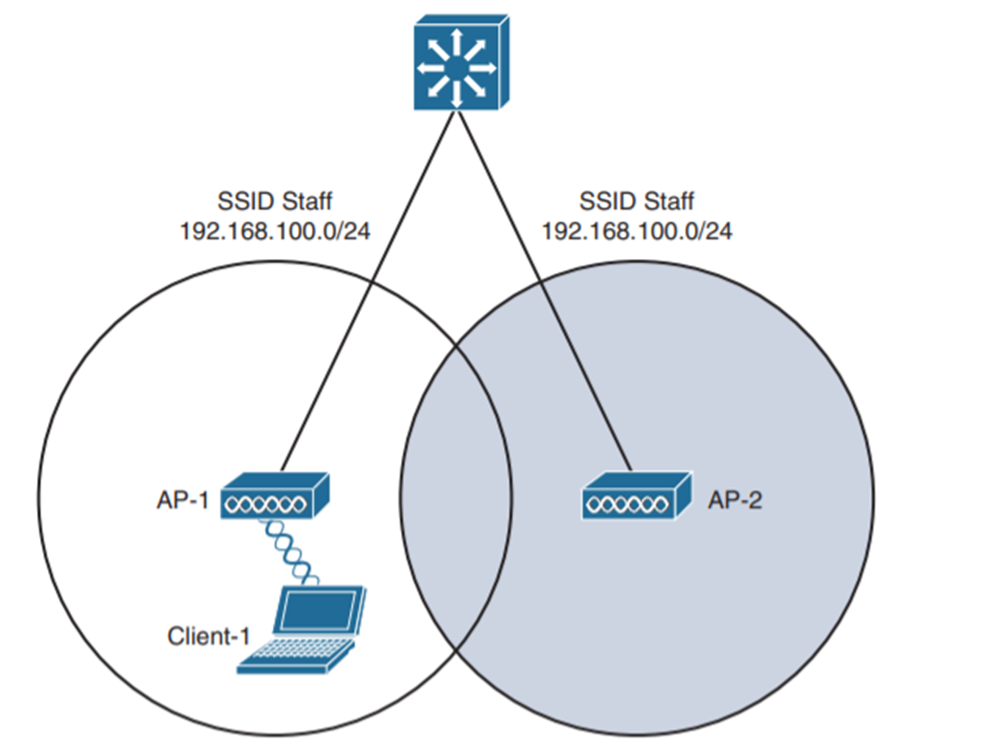
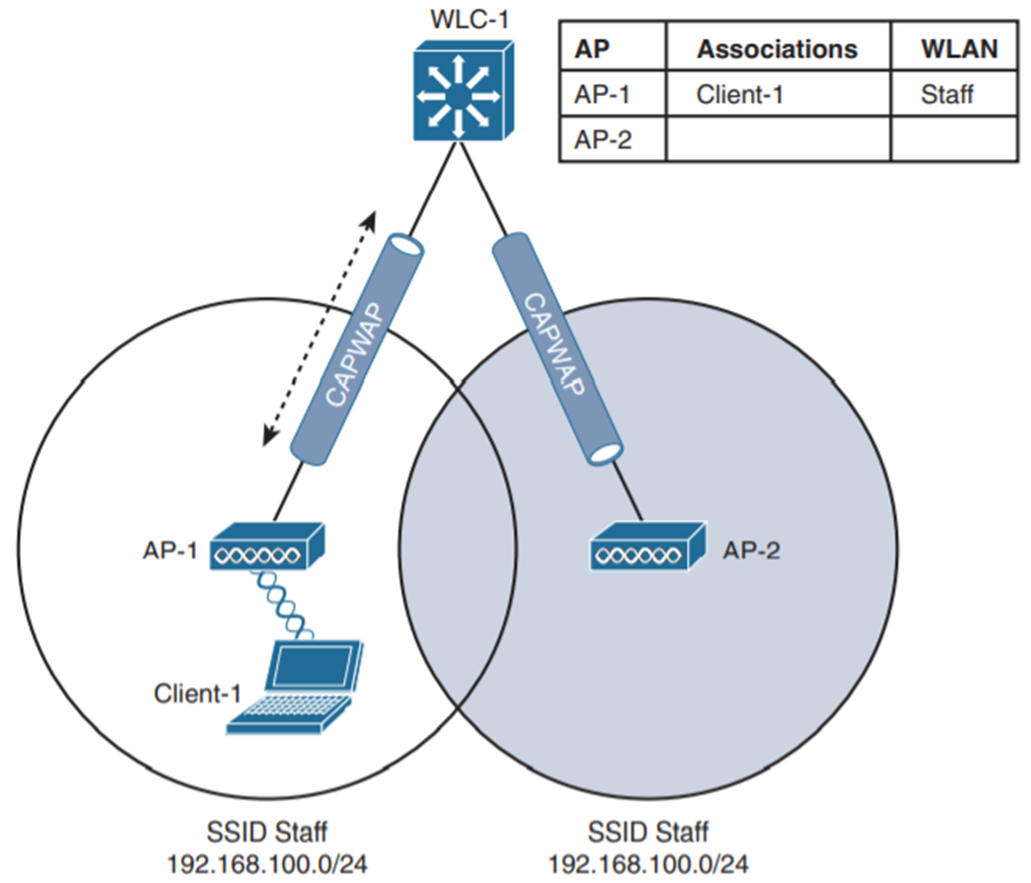
Intra-controller Roaming
It is a type of wireless roaming where a wireless client moves its association from one access point (AP) to another access point (AP) and both of them are connected to a WLAN controller Client roaming is faster and the controller is required to update its association table. Efficient roaming is paramount when time-critical applications are used
Other than the client association, the following instances can occur: In
DHCP, the client can be programmed to refresh the DHCP lease, while in
Client authentication the controller should be configured to use the 802.1x method for client authentication
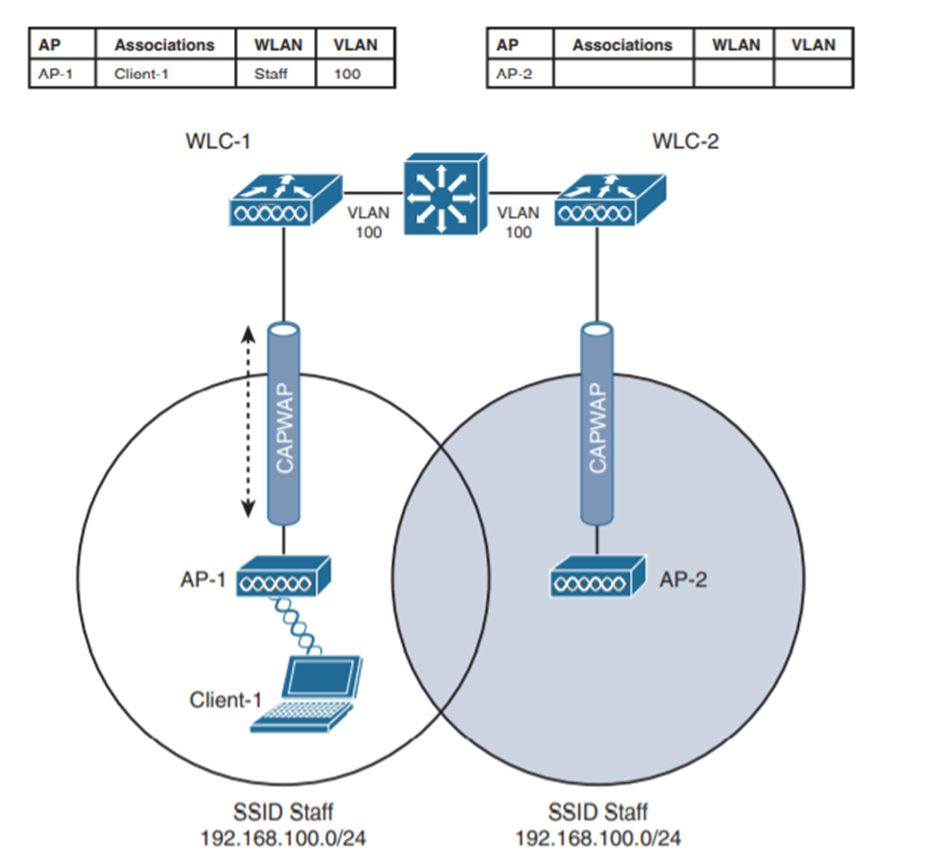
Understanding Wireless Layer 2 Roaming
In Layer 2 Roaming, the two WLAN controllers have to provide the same VLAN with the same subnet. When the client roams to a different access point, it can try to continue using its existing IP address or get a new one from DHCP
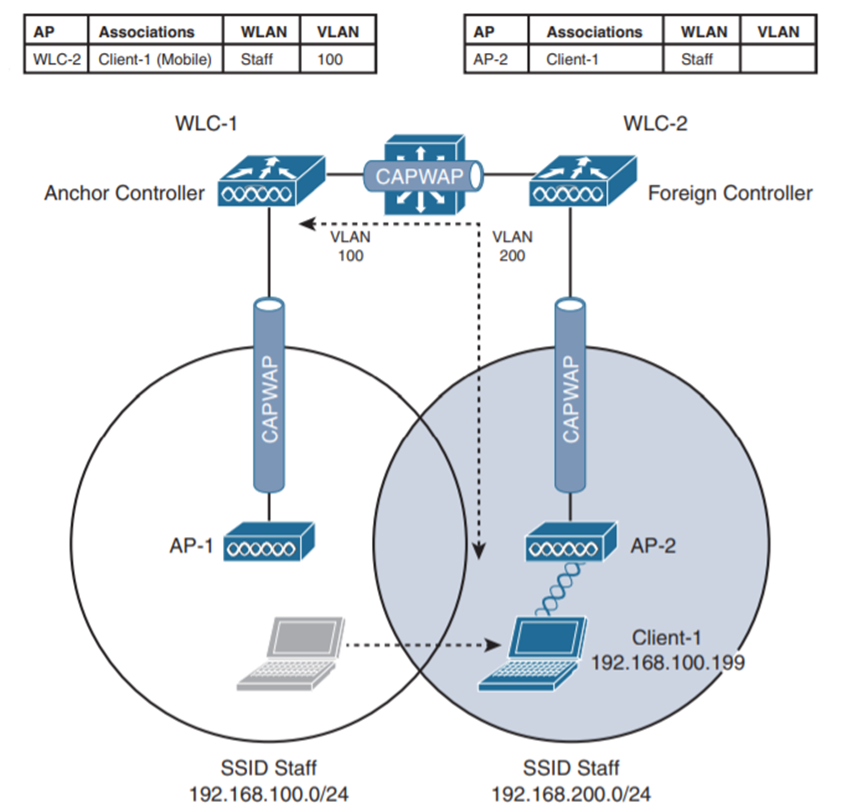
Understanding Wireless Layer 3 Roaming
In this scenario, we would need to roam the client if the second controller is in a different network without even impacting the client service. When a client begins inter-controller roam the two controllers (WLCs) compare their VLAN numbers, if they are similar then it will work like the intra-controller, and if they are not client arranges Layer 3 roams
Handling Authentication during Roam (WLAN Security)
In handling authentication during roaming, basically, there are three types of authentication, they are Cisco Centralized Key Management (CCKM), Key caching, and 802.11r credential caching
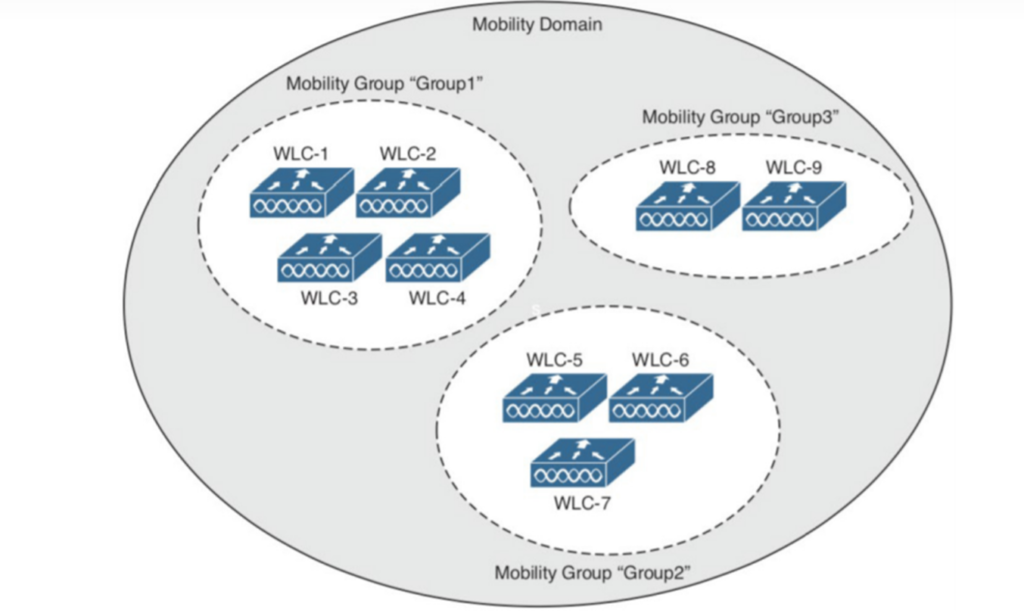
Mobility Groups
There’s a grouping of wireless LAN controllers. Clients can roam quickly when two centralized wireless LAN controllers are configured to belong to the same mobility group. Likewise, if two wireless LAN controllers are configured with two different mobility groups, clients would still roam but not efficient
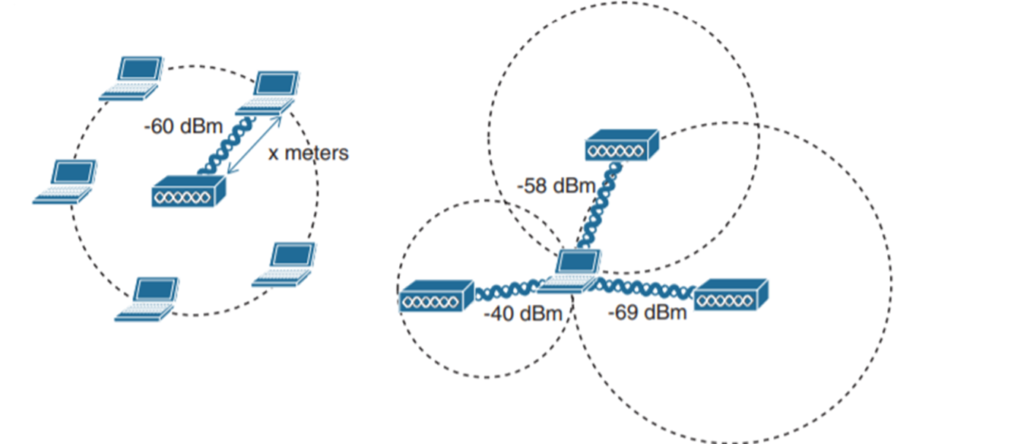
Locating Devices in a wireless network
In order to locate the device in a wireless network, an access point (AP) can use the received signal strength (RSS) of a client device as a measure of the distance between the two. In order to be exact, we have to compare many access point (AP) results
Authenticating Wireless Clients’ WLAN Security
Authentication is paramount in a wireless network, in order to protect against security attacks, such as MITM. The principle is that both the station or wireless client and the network must prove their identity to each other
Open Authentication
Open Authentication is true to its name; it offers open access to a WLAN. The only must-have is that a client must use an 802.11 authentication request before it attempts to associate with an access point (AP). Other than this no other credentials are needed
Authenticating with Pre-Shared Key
In order to secure wireless connections on a WLAN, you have to use one of the WiFi Protected Access (WPA) versions. WPA also known as WPA1, WPA2, or WPA3
Authenticating with EAP
Below gives an illustration of the Extensible Authentication Protocol (EAP):
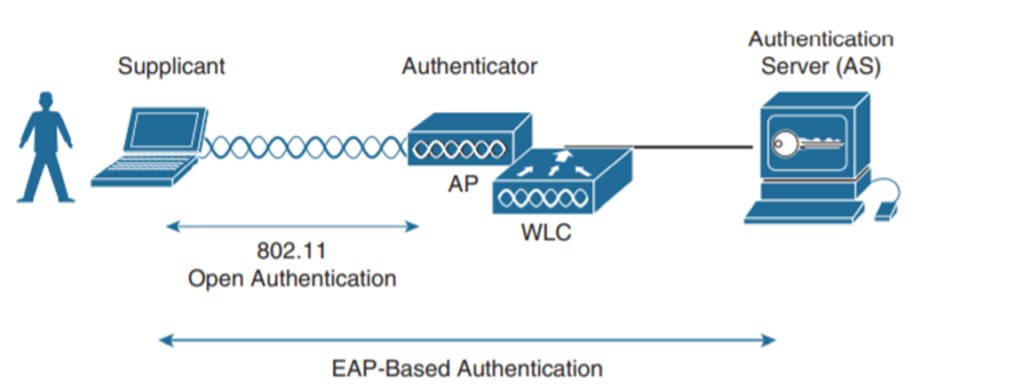
Authenticating with Web-Auth
Web Authentication (Web-Auth) is different because it presents the end-user with content to read and interact with before being given access to the network. For instance, it can present an acceptable use policy (AUP) that the user should accept before being able to access the network

-End-
WLAN and WiFi Infrastructure
Signals and Modulation of WiFi / Wireless
You might also be interested in our free Online Quizzes on all IT topics including Cisco CCNA, Cyber Security, Python Programming, Linux & Ethical Hacking:
Free Online Quizzes (Best for Cisco CCNA, Huawei HCNA, N+)
You can also view free study notes (Cheat sheets) for long term memory:
Networkwalks Summary Cheatsheets
 Understanding wireless & WiFi Roaming is very important in WLAN and WiFi computer networking. It occurs when a wireless client moves around in a region with many access points (APs). It may switch automatically to another access point (AP) with more preferred signal strength.
Understanding wireless & WiFi Roaming is very important in WLAN and WiFi computer networking. It occurs when a wireless client moves around in a region with many access points (APs). It may switch automatically to another access point (AP) with more preferred signal strength.









